You’ve probably wondered what exactly Victoria’s Secret is…An abusive marriage? A child out of wedlock? Substance abuse? Nope. Much worse…After years of suspense…The Question is finally answered, “What, exactly, is Victoria’s Secret?”
Victoria Secret
The Box Office

While the C-5 was turning over its engines, a female crewman gave the G.I.s on board the usual information regarding seat belts, emergency exits, etc. Finally, she said, “Now sit back and enjoy your trip while your captain, Judith Campbell, and crew take you safely to Afghanistan.”
An old MSgt. sitting in the eighth row thought to himself, “Did I hear her right? Is the captain a woman?”
When the attendant came by he said “Did I understand you right? Is the captain a woman?”
“Yes,”! said the attendant, “In fact, this entire crew is female.”
“My God,” he said, “I wish I had two double scotch and sodas. I don’t know what to think with only women up there in the cockpit.”
“That’s another thing, Sergeant,” said the crew member, “We No Longer Call It The Cockpit”……”It’s The Box Office.”
Lil’ ole lady
A farmer stopped by the local mechanic shop to have his truck fixed. They couldn’t do it while he waited, so he said he didn’t live far and would just walk home.
On the way home he stopped at the hardware store and bought a bucket and a gallon of paint. He then stopped by the feed store and picked up a couple of chickens and a goose. However, struggling outside the store he now had a problem – how to carry his entire purchases home.
While he was scratching his head he was approached by a little old lady who told him she was lost.
She asked, ‘Can you tell me how to get to 1603 Mockingbird Lane?’
The farmer said, ‘Well, as a matter of fact, my farm is very close to that house. I would walk you there but I can’t carry this lot.’
The old lady suggested, ‘Why don’t you put the can of paint in the bucket. Carry the bucket in one hand, put a chicken under each arm and carry the goose in your other hand?’
‘Why thank you very much,’ he said and proceeded to walk the old girl home.
On the way he says ‘Let’s take my short cut and go down this alley. We’ll be there in no time.’
The little old lady looked him over cautiously then said, ‘I am a lonely widow without a husband to defend me.. How do I know that when we get in the alley you won’t hold me up against the wall, pull up my skirt, and have your way with me?’
The farmer said, ‘Holy smokes lady! I’m carrying a bucket, a gallon of paint, two chickens, and a goose. How in the world could I possibly hold you up against the wall and do that?’
The old lady replied, ‘Set the goose down, cover him with the bucket, put the paint on top of the bucket, and I’ll hold the chickens.
Mowing & Beer
On Saturday afternoon, I was sitting in my lawn chair, drinking beer and watching my wife mow the lawn.
The neighbor lady from across the street was so outraged that she came over and shouted at me, “You should be hung.!”
I took a drink from my can of Miller Lite, wiped the cold foam from my lips, lifted my darkened Ray Ban sunglasses and stared directly into the eyes of this nosy ass neighbor and then calmly replied, “I am, that’s why she cuts the grass.”
Rye Bread
Two old guys, one 70 and one 77, were sitting on their usual park bench one morning. The 77 year old had just finished his morning jog and wasn’t even short of breath.
The 70 year old was amazed at his friend’s stamina and asked him what he did to have so much energy.
The 77 year old said “Well, I eat rye bread every day. It keeps your energy level high and you’ll have great stamina with the ladies.”
So, on the way home, the 70 year old stops at the bakery. As he was looking around, the lady asked if he needed any help. He said, “Do you have any rye bread?” She said, “Yes, there’s a whole shelf of it. Would you like some?”
He said, “I want 5 loaves.”
She said, “My goodness, 5 loaves, by the time you get to the 5th loaf, it’ll be hard”
He replied, “I can’t believe it, everybody in the world knows about this shit but me.”
Choosing a Wife
A man wanted to get married. He was having trouble choosing among three likely candidates. He gives each woman a present of $5,000 and watches to see what they do with the money.
The first does a total makeover. She goes to a fancy beauty salon, gets her hair done, new makeup; buys several new outfits and dresses up very nicely for the man. She tells him that she has done this to be more attractive for him because she loves him so much.
The man was impressed.
The second goes shopping to buy the man gifts. She gets him a new set of golf clubs, some new gizmos for his computer, and some expensive clothes. As she presents these gifts, she tells him that she has spent all the money on him because she loves him so much.
Again, the man is impressed.
The third invests the money in the stock market. She earns several times the $5,000. She gives him back his $5,000 and reinvests the remainder in a joint account. She tells him that she wants to save for their future because she loves him so much.
Obviously, the man was impressed.
The man thought for a long time about what each woman had done with the money he’d given her. Then he married the one with the biggest tits. Men are like that, you know.
There is more money being spent on breast implants and Viagra today than on Alzheimer’s research. This means that by 2040, there should be a large elderly population with perky boobs and huge erections and absolutely no recollection of what to do with them.
Getting Older
An elderly couple had dinner at another couple”s house, and after eating, the wives left the table and went into the kitchen.
The two gentlemen were talking, and one said, “Last night we went out to a new restaurant and it was really great. I would recommend it very highly.”
The other man said, “What is the name of the restaurant?”
The first man thought and thought and finally said, “What is the name of that flower you give to someone you love? You know… the one that”s red and has thorns.”
“Do you mean a rose?”
“Yes, that”s the one,” replied the man. He then turned towards the kitchen and yelled, “Rose, what”s the name of that restaurant we went to last night?
Cajun Math
A Cajun man wants a job, but the foreman won’t hire him until he passes a little math test. Here is your first question, the foreman said. “Without using numbers, represent the number 9.” “Without numbers?” The Cajun says, “Dat is easy.” And proceeds to draw three trees.
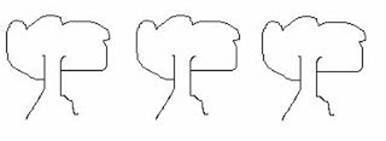
“What’s this?” the boss asks “Ave you got no brain? Tree and tree and tree make nine,” says the Cajun.
“Fair enough,” says the boss. “Here’s your second question. Use the same rules, but this time the number is 99.” The Cajun stares into space for a while, then picks up the picture that he has just drawn and makes a smudge on each tree. ; “Ere you go.”
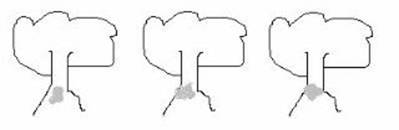
The boss scratches his head and says, “How on earth do you get that to represent 99?” “Each of da trees is dirty now. So, it’s dirty tree, and dirty tree, and dirty tree. Dat is 99.”
The boss is getting worried that he’s going to actually have to hire this Cajun, so he says, “All right, last question. Same rules again, but represent the number 100.” The Cajun stares into space some more, then he picks up the picture again and makes a little mark at the base of each tree and says, “Ere you go. One hundred.”
The boss looks at the attempt. “You must be nuts if you think that represents a hundred!” The Cajun leans forward and points to the marks at the base of each tree and says, “A little dog come along and poop by each tree. So now you got dirty tree and a turd, dirty tree and a turd, and dirty tree and a turd, which make one hundred.” The Cajun is the new supervisor.
Morals
I was a very happy man.
My wonderful girlfriend and I had been dating for over a year, and so we decided to get married. There was only one little thing bothering me…It was her beautiful younger sister. My prospective sister-in-law was twenty-two and gorgeous. One day her ‘little’ sister called and asked me to come over to check the wedding invitations.
She was alone when I arrived, and she whispered to me that she had feelings and desires for me that she couldn’t overcome. She told me that she wanted me just once before I got married and committed my life to her sister. Well, I was in total shock, and couldn’t say a word.
She said, “I’m going upstairs to my bedroom, and if you want one last wild fling, just come up and get me.”
I was stunned and frozen in shock as I watched her go up the stairs. I stood there for a moment, then turned and made a beeline straight to the front door. I opened the door, and headed straight towards my car.
Low and behold, my entire future family was standing outside, all clapping!
With tears in his eyes, my future father-in-law hugged me and said, “We are very happy that you have passed our little test. We couldn’t ask for a better man for our daughter. Welcome to the family.”
And the moral of this story is: Always keep your condoms in your car.
Interesting Cars
Yesterday I drove to Narita airport and after I parked my car I happened to notice a couple interesting cars in the parking lot, so I had to take a couple photos. The yellow car is called a smart car. It looks extremely small and compact. I think you may fit one comfortably and a briefcase. This car is in Japan, so maybe you could fit two Japanese people comfortably. The 2nd car, I have no idea what kind of car it is, but I thought the rear window was unique. The overall shape of the car was pretty unique.


Bacon Grease Warning, Please Read!

The question is: Do you use bacon grease?
We were raised on bacon grease (lard) as kids and even into adulthood. I will never use it again. I hope you will throw yours away whenever you fry bacon from now on. It seems as though nothing is safe to eat anymore.
Cooking With Bacon Grease
I just threw out my last 2 tbsp of bacon grease! This is what happens when you keep cooking with bacon grease. This is a warning. It could happen to you…
Bacon grease will make your feet small! Warn everyone!
Network Testing Programs
[Abstract]
The purpose of this document is to explain different types of testing programs that can be used to identify network latency issues when planning a network upgrade. Also included within this document are naming conventions for networking devices and hosts. Lastly this document will outline and explain different types of equipment and their roles as they pertain to network security based upon a provided scenario.
[Introduction and background]
Mr. Smith is the Director of IT at a law firm located in downtown Chicago. He needs to plan for a network upgrade. He has decided that he would like to have a network analysis done before the upgrade so that he can find out which systems would require upgrades and to create a strategy to present to the senior partners that will include return on investment.
The law offices occupy four floors of a high-rise building. The customer is experiencing network latency, especially in the Accounting department and in Human Resources, which both reside on the 32nd floor. The director of the Accounting department has expressed concerns about the security of his files. The Research, IT, and Corporate Administration departments all share the 33rd floor. The senior and junior partners and their support staff occupy the 35th floor, and the 36th floor is used for reception and conference rooms. The firm has decided that video conferencing is an essential component of its business and is looking to implement video conferencing as soon as possible so it can communicate with two new satellite offices that will be occupied in six months.
The firm has one network segment for each floor, but has been experiencing latency. Each floor except the 36th has 10 to 20 printers. Each floor has a 100Mb uplink to the Data Center on the 33rd floor. There are approximately 50 PCs on the 36th floor, 150 PCs on the 35th floor, and 40 PCs on both the 32nd and 33rd floors. The servers for each department reside on their respective floors. Mr. Smith is concerned about network security and wants a recommendation to secure traffic of three specific departments: Human Resources, Accounting, and Corporate Administration.
[Recommended testing program (Prototype or Pilot)]
When testing a network to get a complete understanding of issues the network may be having there is no silver bullet application, but rather a combination of applications that have specific functions. The first thing that is a major concern with understanding possible issues that are happening on a network is possible bottlenecks or bandwidth limitations as they pertain to network performance. One application that performs a secure real-time network monitoring is called “nettest (Agarwal, Boverhof, Jackson).” This open-source application designed to run on Linux platform and it incorporates a few different frameworks to conduct a series of tests as they pertain to network performance. This application is designed to work between a couple different hosts on a network so prior to using it; authorization must be attained in order to install the application between hosts. Once the performance testing is complete, it is important to know what is being sent accrossed the network. To determine what is being sent accrossed a network a packet sniffer can be used. A good useful free network packet sniffer is called “Wireshark (Sharpe, Warnicke, 2008).” Wireshark allows to packets to be captured and dumped into a file where they can be analyzed at a later point in time or for somebody with fast eyes they can analyze the packets in real-time. For both types of tests, it is recommended to perform the tests over a period of time such as over a 24-hour period. This will help to understand the demands placed on the network during peak hours as well as non-peak hours of operation. The use of multiple programs to analyze network performance and breakdown of the types of network traffic will help to identify any issues.
[Naming Structure]
When naming network devices it is important to give a device a name that can identify whom the device serves and the devices location. To identify whom the device serves there is not enough space within the devices name space to allow for complete names, so abbreviations are going to have to be used (Morris, 2008). For example the human resources department has a 3 letter designator HUM, accounting ACC, administration ADM, sales SAL, information technology INF, shipping SHI, corporate COR, and so on. To identify a devices location a building number, floor number, and room number can be used. Finally if it is desired a device can be identified by the device and if it is an internal or external device by using the identifiers SW for switch, R for router, B for bridge, W for workstation, or SE for server. When all of these abbreviations are put together a possible name for a device can look like this: ACC-115-32-J-SWI. This methodology tells somebody that this device is found in the accounting department of building 115, located on the 32nd floor in room J, and it is an internal switch. Following naming structure helps identify devices, their functions, and where they are located.
[Adequacy of security for the data in each department]
No matter which company, which organization, or which department somebody works for; there is always a need to keep data secure. Even though people work for the same company doesn’t mean they need access to the same data. One method to keep different departments from accessing each other’s data is by logically separating the network via the use of virtual LANS otherwise known as VLANs. Using VLANs keeps each department segmented so that only personnel within a particular department can access only that department’s data. Another way to keep data secured is for data that is stored in a centralized location, like a file server, is by the use of file permissions. Personnel without the correct permissions will not be able to access a particular file. It is also important to ensure data is being transported securely acrossed a network. To ensure data is being transmitted securely on the network, IPSec can be used. IPSec encrypts packets of information so that it can reach the intended destination securely. Finally it is important to ensure no outside access is allowed on the network. To prevent unauthorized access to a network, a firewall can be used. A network firewall inspects every packet it receives by checking the source and destination of each packet, and then it checks an access control list (ACL) to verify access is allowed before the packet is forwarded onto the destination.
[Functions of each network device]
Different networking devices function at different layers of the OSI model and therefore each can do their own part in ensuring a network is secure. Starting at the lowest level of the OSI model and working toward the top we can see what each device does and what added security it can provide. Physical security plays an important part of ensuring the physical connectivity is secured within a controlled area. Switches function at the data-link layer of the OSI model and their responsibility is to transport data quickly and efficiently. Switches also provide network security by allowing a network to be segmented into different VLANs. Routers function at the network layer of the OSI model and their function are to transport data from one network to another. Routers can provide a little security by providing an ACL to ensure network traffic from one network is authorized to access another network. Network firewalls also function at the network layer and their main purpose is to ensure both that traffic is authorized from one network segment to another, but also a firewall blocks any unused network ports from being accessed. Networked servers can function at the session, presentation, and application layers of the OSI model. A properly configured network server can provide security be ensuring packets are encrypted, authorized users are allowed to access a network by authenticating users, and files are secured with the correct file permissions. Each device on a network plays it own role to ensuring access to a network is authorized and data within the network is secured.
[How needs of key departments change with the network design]
Even though different departments work for the same company their specific needs may influence the design of a network. The most obvious specific need for a department is the amount of users the department has. Since the senior and junior staff of the law firm occupies the 35th floor with 150 different computers, they may have a higher demand for bandwidth than the accounting and human resources departments, which occupy the 32nd and 33rd floors with only 40 computers. The IT and research departments may both have specific needs of having the need to put their own networking devices on the network to allow for them to create a test network. The corporate department may want to use voice over IP services and therefore have a specific need of having a voice VLAN configured on their networking devices. No matter what the specific need of a department is, a good network design must incorporate all of the departments needs for both today and into the future.
[Conclusion]
In conclusion, to best identify issues pertaining to the law firm’s network a couple different tools should be used to both identify any possible bandwidth issues or issues pertaining to the types of traffic being passed along the network. Different departments within the law firm have different needs and therefore each network segment should be designed to accommodate each department’s needs. The company’s current network security is inadequate, so network security should be implemented at multiple layers of the OSI model to ensure all communications and data is secure. Each device within the network topology can play a specific role to ensuring the network is secure.
[References]
1. Agarwal, Boverhof, Jackson, Deb, Joshua, and Keith Nettest: Secure Network Testing and Monitoring. Retrieved September 27, 2008, from Nettest: Secure Network Testing and Monitoring Web site: http://acs.lbl.gov/~boverhof/nettest.html
2. Sharpe, Warnicke, Richard, Ed (2008). Wireshark: Go deep. Retrieved September 27, 2008, from Wireshark: Go deep. Web site: http://www.wireshark.org
Morris, Michael (2008, January 10th). Naming Conventions | NetworkWorld.com Community. Retrieved September 27, 2008, from Naming Conventions | NetworkWorld.com Community Web site: http://www.networkworld.com/community/node/23721
Menopause Jewelry
My husband, being unhappy with my mood swings, bought me a mood ring the other day so he would be able to monitor my moods. We’ve discovered that when I’m in a good mood, it turns green. When I’m in a bad mood, it leaves a big frickin red mark on his forehead. Maybe next time he’ll buy me a diamond. Dumb ass.
He Wore His Collar Backwards
A little boy got on the city bus, sat next to a man reading a book, and noticed he had his collar on backwards. The little boy asked why he wore his collar backwards.
The man, who was a priest, said, “I am a Father.”
The little boy replied, “My Dad doesn’t wear his collar like that.”
The priest looked up from his book and answered, “I am the Father of many.”
The boy said‚ “My Dad has 4 boys, 4 girls and two grandchildren and he doesn’t wear his collar that way.”
The priest, getting impatient, said‚ “I am the Father of hundreds” and went back to reading his book.
The little boy sat quietly thinking for a while, then leaned over and said, “Maybe you should use a condom and wear your pants backwards Instead of your collar.”